-
![The "Golden Key" to IT Career]() 2025-10-28 The "Golden Key" to IT Career
2025-10-28 The "Golden Key" to IT CareerHuawei ICT, CCNA and CKA certifications form a golden certification combination in the IT field, covering three core technical areas: traditional networking, cl...
read more > -
![Golden Combination: Full-Stack Skills fo]() 2025-10-27 Golden Combination: Full-Stack Skills fo
2025-10-27 Golden Combination: Full-Stack Skills foHuawei ICT, CCNA and CKA certifications together form a golden combination in th
read more > -
![Build Full-Stack IT Skills and Broaden C]() 2025-10-25 Build Full-Stack IT Skills and Broaden C
2025-10-25 Build Full-Stack IT Skills and Broaden CHuawei ICT, CCNA and CKA certifications form a golden combination, accurately co
read more > -
![Three Certifications, Unlimited Potentia]() 2025-10-24 Three Certifications, Unlimited Potentia
2025-10-24 Three Certifications, Unlimited PotentiaBuilding Versatile Skills and Broadening Career PathsCertifications like Huawei
read more > -
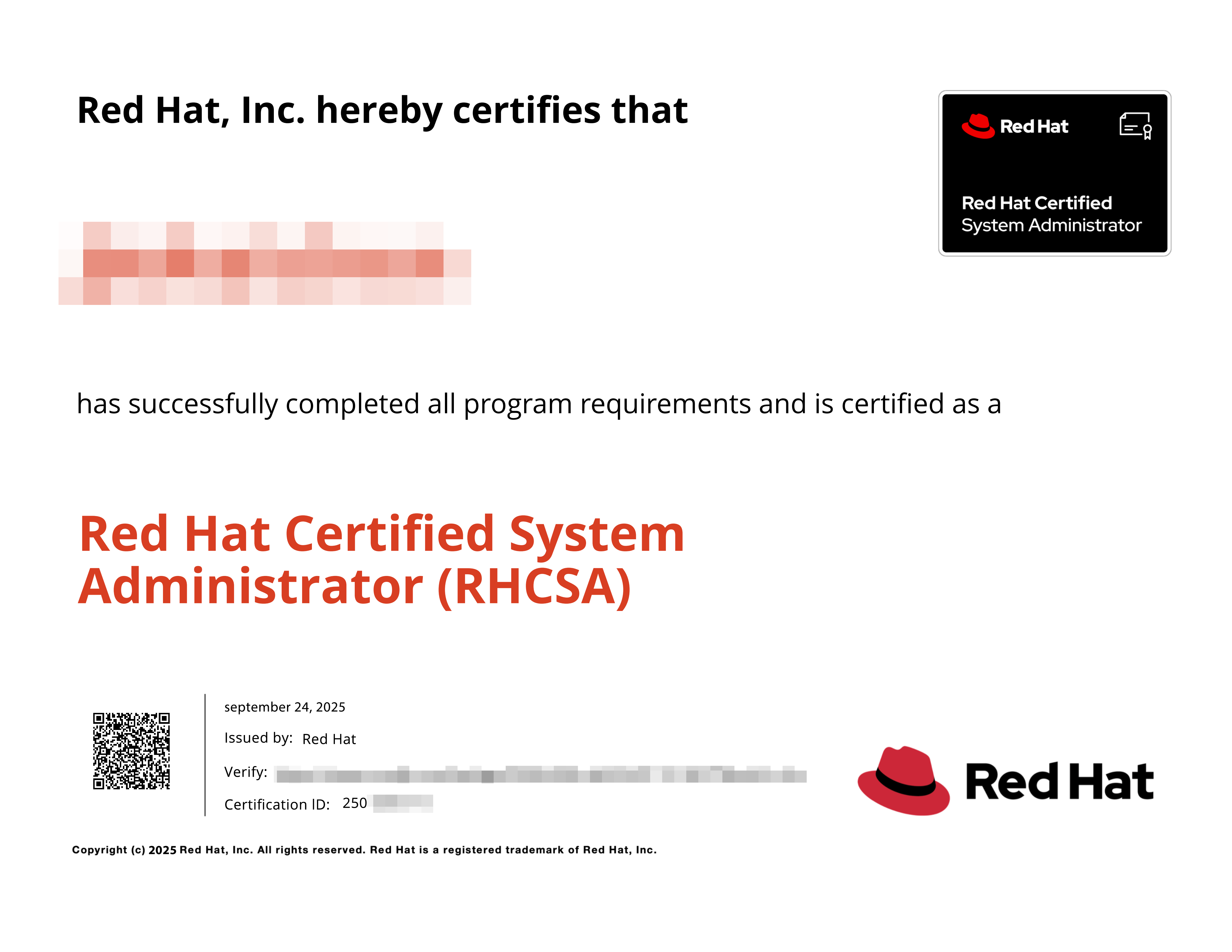
![Huawei, Cisco, Red Hat: Three Pillars fo]() 2025-10-23 Huawei, Cisco, Red Hat: Three Pillars fo
2025-10-23 Huawei, Cisco, Red Hat: Three Pillars foIn the competitive landscape of the IT workplace, the technical and certificatio
read more > -
![CKA Certification: "Ops Passport&qu]() 2025-10-22 CKA Certification: "Ops Passport&qu
2025-10-22 CKA Certification: "Ops Passport&quIn the era of rapid development of cloud-native technology, the CKA certificatio
read more > -
![Huawei IT Certifications: "Hard Cur]() 2025-10-21 Huawei IT Certifications: "Hard Cur
2025-10-21 Huawei IT Certifications: "Hard CurHuawei IT skill certifications have become "hard currency" for profess
read more > -
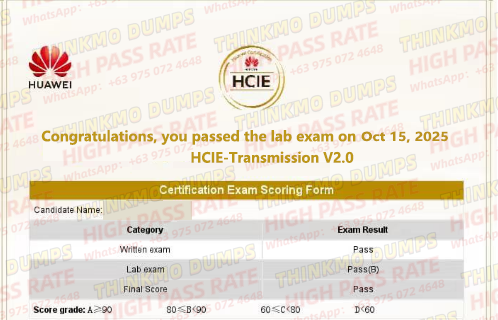
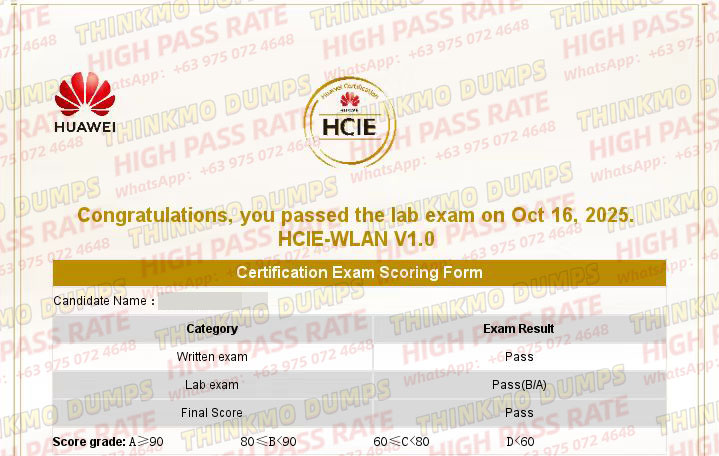
![HCIE-WLAN V1.0 & Huawei IT: Drive IC]() 2025-10-20 HCIE-WLAN V1.0 & Huawei IT: Drive IC
2025-10-20 HCIE-WLAN V1.0 & Huawei IT: Drive ICHuawei IT: The Core Engine Empowering Career GrowthIn today's era of acceler
read more > -
![Huawei AI and Storage Certification Exam]() 2025-10-18 Huawei AI and Storage Certification Exam
2025-10-18 Huawei AI and Storage Certification ExamGreat News: Huawei AI and Storage Certification Exams Achieve Outstanding Result
read more >