The firewall that the system comes with. Exe software to kill how do you do?
Good afternoon, my friends!
Today , let 's talk about a very common but often overlooked problem in everyday use of Windows systems : how to deal with the system 's built-in firewall or security mechanism to remove the .exe installation file or registration file ?
This problem is particularly easy to occur in some shelled shell , registration mechanism , online activation tools , especially some niche software or test tools , often be Windows Defender or third-party security software directly " processed " , failed to install .
For more information, please scan the WhatsApp QR code below to contact customer service.

You may have encountered these situations:
· It was plainly regular software, but it was "killed" when you double-clicked the installer;
· As soon as the registration code is entered, clicking the registration button pops up "Program exceptionally terminated";
· Downloaded..exeThe file was gone as soon as it was uncompressed;
· Even prompted "operation failed, file could not be found," and then didn't even leave the Recycle Bin.
Why would they be "missed"?
This is due to the "protective" role of the system's security policies, especially the following components:
Component Name
| Explanation of role
|
Windows Defender
| The system comes with an antivirus tool that scans and blocks suspicious things..exefile
|
Smart Screen
| Block an unknown publisher program with a blocking prompt
|
Control rights
| Higher permissions are required to run or write to some directories (such as C:\ Windows, C:\ Program Files)
|
Third party antivirus software
| More "sensitive" than the system, it may actively isolate or even delete files
|
What to do? Here's the solution.
Option 1: Temporarily shut down Windows Defender
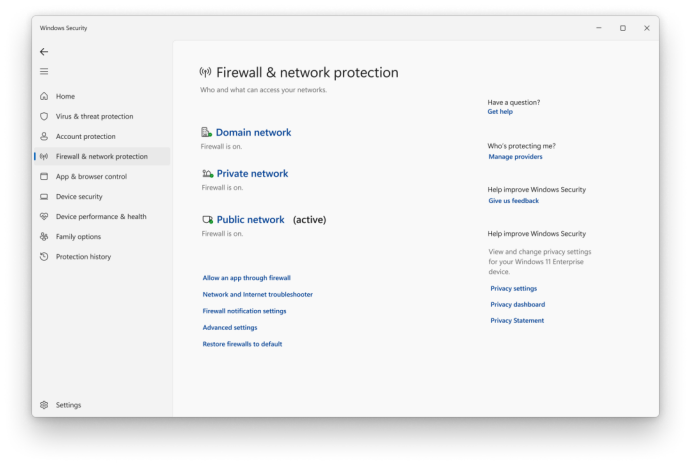
1. Open Settings > Privacy & Security > Windows Security Center;
2. Click on "Virus and Threat Protection";
3. Select "Manage settings";
4. Turn off real-time protection temporarily.
It is recommended to turn on after installation is complete to prevent long-term shutdown from causing system risk.
Option 2: Add documents to the white list
If you trust this,.exeDocuments
1. Also in "Virus and Threat Protection";
2. Select "Permitted Threats" or "Protect History."
3. Find the program that was isolated and click "Restore";
4. Then add it to the Exclusions, either the path or the entire folder.
Option 3: Turn off the SmartScreen filte
1. Control panel > Internet Options > Advanced;
2. Or go to Settings > Privacy and Security > App and Browser Control;
3. in“SmartScreen for Microsoft Edge"and" Microsoft Store Apps, "select" Do Nothing. "
It is only suitable for use with offline activation or test tools, and it is not recommended to shut down online applications.
Option 4: Use Compatibility Mode / Administrator Run
Some registration procedures requireadministrative privileges:
· Right click.exeFile > "Run as administrator";
· Or: Right-click Properties > Compatibility > Select Compatibility mode to run.
Option 5: Redownload from a trusted source
if.exeThe file is really permanently deleted and can't be recovered from the Recycle Bin. You can try:
· Go to the official website and download the package again.
· Go to GitHub or official website forums provided by software developers to obtain the original package;
· Check if there are any.zipor.rarThe backup file in the compressed package;
Try to avoid downloading from unidentified websites to prevent secondary infection.
remind
· For installation programs , registration tools , and configuration tools , it is recommended tostore them in a directory that is not easily scanned( such asD:\Tools\);
· Try to avoid double-clicking to open unknown sources.exeDocuments;
· If you are a system administrator, it is recommended to create exception rules through Group Policy or Security Policy;
· Turn on protection in time after installation to prevent real viruses from invading!
That's it for todayIn network operation or daily use, it is very common to encounter software "killed," as long as you master the strategy, many timescan be avoided and restored。Hope this article is helpful to you
If you find it useful, remember to share it!
For more operation and maintenance resources, follow the Facebook account&youtube account: Thinkmo Dumps


